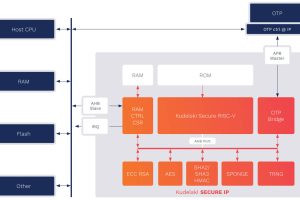
The QDID PUF is hardware silicon IP that harnesses quantum tunnelling current variations on a standard CMOS process as a source of entropy. The PUF provides multiple, internally generated unclonable identities. These are consistent, device-specific outputs for a given input (challenge), making them suitable for applications that need repeatable, unique identifiers or keys tied to a specific hardware instance.
The TRNG produces unlimited new, unpredictable random numbers each time it is used, which is essential for many cryptographic operations that require fresh randomness. Examples of these are session keys for protocols like TLS/SSL and cryptographic protocols that require nonces (numbers used once) or initialisation vectors.
 “Side-channel attacks continue to pose a growing threat to connected devices and IoT networks,” says CEO Shahram Mossayebi (pictured), “the source of entropy is particularly vulnerable to such attacks yet is often neglected. The QDID PUF and TRNG provide the ultimate protection against such risks because of the unique characteristics of gate tunnelling as a source of entropy
“Side-channel attacks continue to pose a growing threat to connected devices and IoT networks,” says CEO Shahram Mossayebi (pictured), “the source of entropy is particularly vulnerable to such attacks yet is often neglected. The QDID PUF and TRNG provide the ultimate protection against such risks because of the unique characteristics of gate tunnelling as a source of entropy
In practice, many secure systems use PUFs and TRNGs together. For example, a PUF might be used to generate a root key for a device, while a TRNG is used to generate session keys or other ephemeral random values needed during the device’s operation.
QDID eliminates costly secret key injection processes. Identities and keys are not stored in memory, where they are vulnerable to side-channel attacks, and cannot be counterfeited, copied or hacked, even in a post-quantum era. As a result, QDID offers a secure foundation for a root-of-trust in any IoT device.
The QDID IP has passed CC EAL4+ tests following an independent 3rd party assessment provided by eShard. The assessment of electromagnetic emissions of the IP proved that there is no correlation with either the tunnelling current variation as the source of entropy or the cryptographic secret keys generated in the semiconductor.
QDID has been verified for use with standard CMOS manufacturing processes at nodes from 55 nm down to 12 nm. It generates seeds of between 64 and 256 bits. At 22 nm, it requires a silicon area of less than 0.15 square mm and is approved for use with TSMC, UMC and Global Foundries CMOS processes. Other certifications include NIST SP 800-22 verification for randomness and PSA Level 2 Ready.
 Electronics Weekly
Electronics Weekly